Working Steps of Enstella Word Password Recovery Software
Working Procedure of Word Password Recovery Tools
Step-by-step Enstella Word Password Recovery Software Working & See how its working and Recover Lost Word File Password
Enstella Word Password Recovery tool is the best doc Unlocker program which efficiently Recover and Unlocke Word file Password.
Launch Enstella Word Password Recovery Software (Go toStart ->Programs ->Enstella Word Password Recovery-> Enstella Word Password Recovery).
Just follow the following instructions step by step to Recover Word File Password
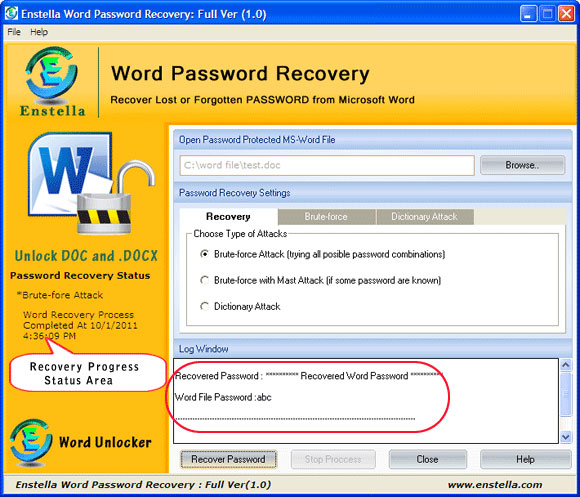
ClickBrowse button to select the your password protected Word *.doc or *.docx file as shown below

After selecting the appropriate protected Word file, the software looks like below-

- Password Recovery Settings
- Enstella Word Password Recovery Software having 3 types of Password Recovery Attacks, these are as below-
- Brute Force Attack (Trying all possible password combinations)
- Brute Force with Mask Attack (If some password are known)
- Dictionary Attack
- Enstella Word Password Recovery Software having 3 types of Password Recovery Attacks, these are as below-
1) Brute Force Attack- It means the program will do a full-scale search and try all possibilities randomly in order to get the password guess match with the correct password and recover it. However, this mode is not as efficient as the other two attacks when the password is strong enough. As the length of the password increases, so does the number of possible passwords. In this way the program will do a lot more times of guess tests.

2) Brute Force with Mask Attack -What isMask? In the field of decryption, mask is a commonly used term referring to the password features you still remember. For example, the possible password length, any digits, letters, special characters like pond, dollar, or asterisk in the password. What is the first and last characters of the password, etc. This allows users to define a password mask to minimize the guess test load and maximize the recovery speed. You can use this attack if you still remember any part of your excel password. For example, if you still remember your password is 4 characters and begins with "z", then you can define the mask as "z???". Thus reduces the detecting scale for the program, as it will only seek for the last 3 characters instead of 4 characters of the whole. To use this attack, a password mask must be defined.

3) Dictionary Attack -This attack is highly recommended as it offers a smarter access to the password recovery. If use properly, it is the fastest when compared with the above two attacks. This attack is intended to seek the possible password based on a dictionary. Then what's a dictionary? Dictionary is a notepad file, which can be simply interpreted as a library listing the password elements. The program will just base on this dictionary to detect the password. This dictionary can be the integrated one or the one you create. The integrated dictionary is a notepad file listing common character combinations, such as a, ab, 123, 4, AB, etc. that people may frequently use for passwords. You can also create a dictionary by listing character sets that you frequently use to let the program base on when seeking passwords, such as your name, birthplace, birthday, etc. If so, the seeking scope will be largely reduced and it is deemed to save time for the process.

Reveal Word Password- When you finished the settings of recovery attacks, then click on button to reveal the original Word Password.
button to reveal the original Word Password.
Note: Our Word Password Recovery software easily reveal Word (doc and docx) Passwords from MS Word 2016, 2013, 2010, 2007, 2003, 2002(XP), 2000, 97 and 95 files.
